Posts
10894Following
416Followers
657PFP by @zombineko@furaffinity.net
Opinions expressed in this profile are representative of those of your employer.
Furry Code
FPR4a A C->+ D>++ H+++ M- P++>++++ R- T+++ W- Z- !S RLCT a cl+++ d e+>++ f++++ h- iwf+++ j p-->- !s

rail 🦊
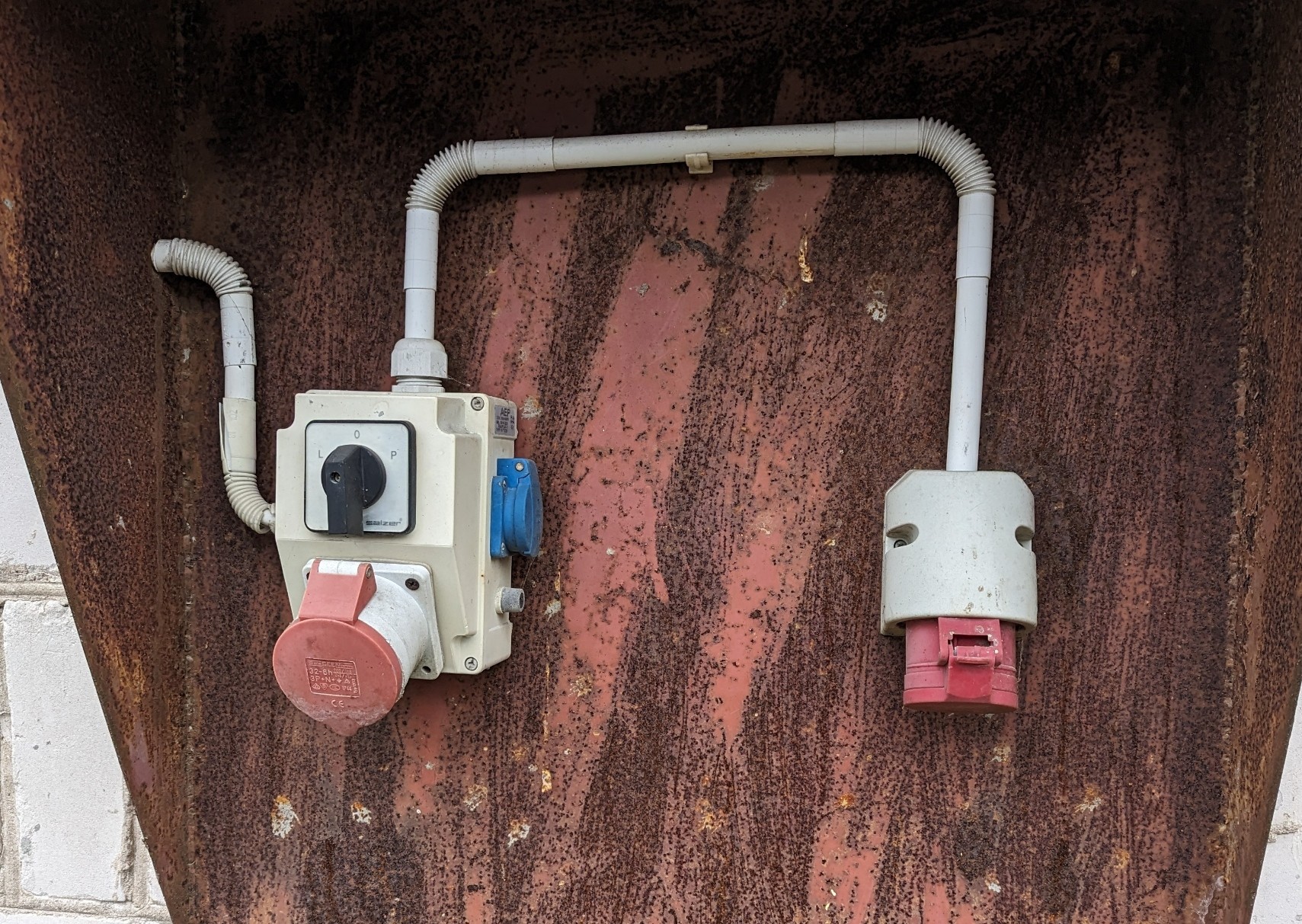
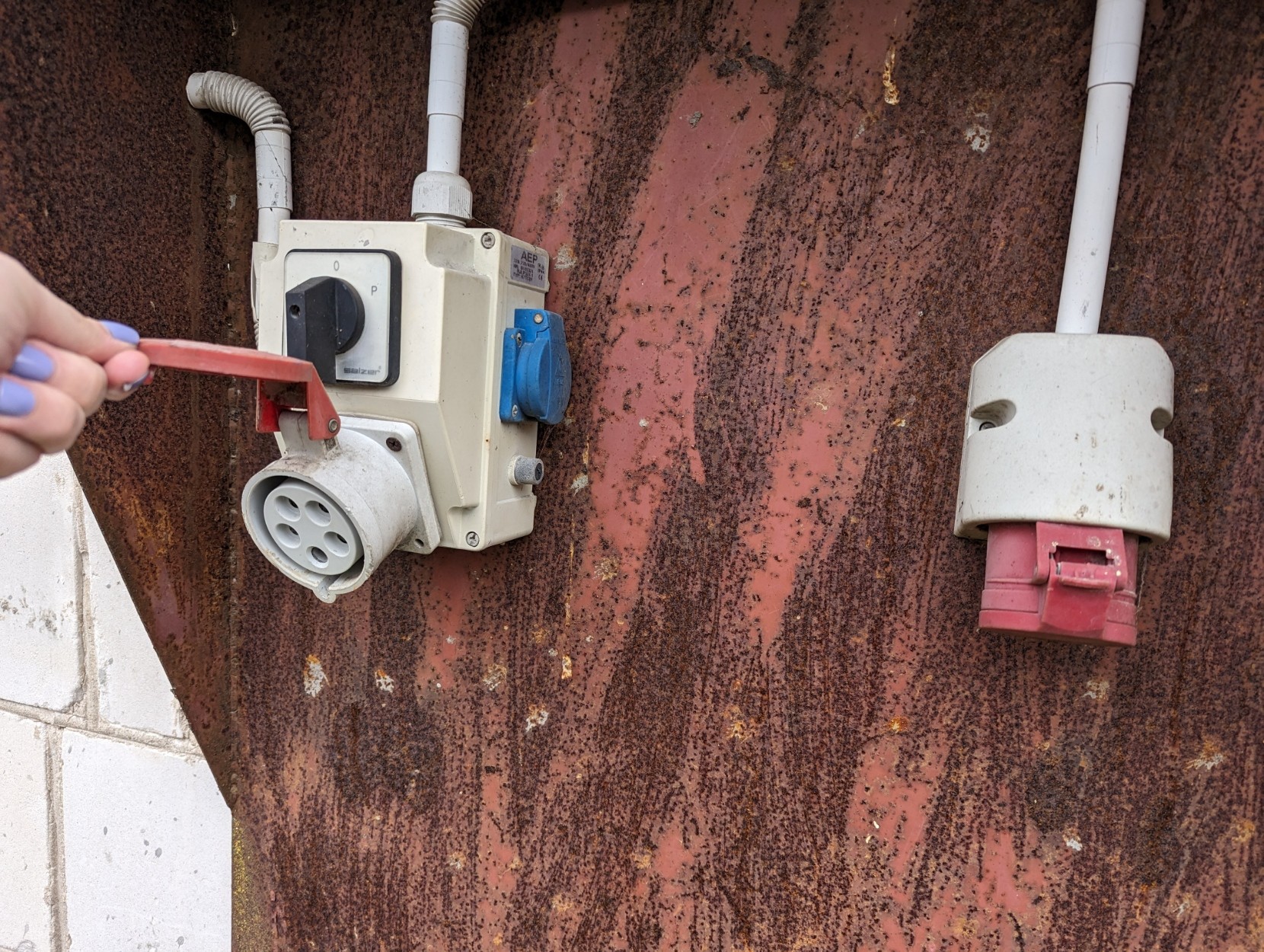
rail_@bark.lgbtNot safe for Americans: casual 400V (total) 3-phase 32A high-power outlet in European household

Atapi.EXE
sterophonick@bitbang.socialthis calc test is gonna be wacky af tomorrow it's at FIVE PM
Charlotte 🦝 
charlotte
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAaAAAABNl
Y2RzYS1zaGEyLW5pc3RwMjU2AAAACG5pc3RwMjU2AAAAQQSCO0Hw8/ScfjT1JVEP
F+IIOp+jFH95q/C017pOYLqaO4p72ySjXE4YQBuHgKXRHNqSInpRIP1iMEDsoyEv
XudAAAAAoMVXtS3FV7UtAAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAy
NTYAAABBBII7QfDz9Jx+NPUlUQ8X4gg6n6MUf3mr8LTXuk5gupo7invbJKNcThhA
G4eApdEc2pIielEg/WIwQOyjIS9e50AAAAAhAJ9a7QDVSL1sWFzLkhvAH/OH7UcZ
wMoFSyQ0HxH8nog7AAAAAAECAwQFBgc=
-----END OPENSSH PRIVATE KEY-----
ssh into x@whoami.filippo.io

Franziska
kunsi@chaos.socialGleisbogen oder so, keine Ahnung ich mach nix mit Bahninfrastruktur
Charlotte 🦝 
charlotte
Show content
you can save 100% on deodorant by using the all natural deodorant that a skunk can provide
Charlotte 🦝 
charlotte
i think people calling for 1:1 translation should try learning the language something is translated from before declaring that’s how translation should work. it doesn’t and for many good reasons.


hacker witch puck 👩💻
puckipedia@puckipedia.comokay so. nix 2.24+ vuln: nar unpacking is fucked, and local unprivileged users, or any binary cache you have configured, can just Get Root on your system
if you create a nar file with a directory containing both a symlink and a directory with the same name, the symlink will be followed and filled with the contents you put in that directory due to a refactoring mistake
and, as the nix daemon usually runs as root (with the nix store mounted read-write), it's possible to write files into e.g. /run/current-system/etc/systemd/system. and as such, and get persistent root access from unpacking a malicious NAR.
now do you make Nix read a NAR? well... there's two primary ways
any untrusted user that can talk to the nix daemon can write NARs that are either content-addressed, or signed by a trusted key, into the Nix store;
...and any binary cache can do this as well, as the daemon will fetch nar files from the binary cache.
now this vuln would be evil but local privesc only if this was all, except for a very funny second issue:
the signature on NAR files is validated only *after* unpacking the NAR
so any malicious binary cache can reuse the signature of, say, a store path on cache.nixos, and (this is very likely, of course) if the nix daemon trusts the signature, it will end up unpacking any nar of the cache's choice without checking that the signature (or even hash!) matches
in certain cases (e.g. there's a symlink pointing to root in a trusted nar) this can even be done entirely silently, which is .. very bad.
at this point the disclosure timeline has passed; and a point release was even made after the vulnerability was well known by the entire team (GHSA-h4vv-h3jq-v493 was opened a day before the point release); and the severity of the vulnerability is high enough that i want people to be aware of this issue

Charlotte 🦝 
charlotte
⚠ this account is known to the state of california to cause the urge to pet
Charlotte 🦝 
charlotte
I am looking for accountant interns in my new finance startup called “taking the money and run”. this is a reverse financed internship. you need to pay me $400 a month to participate
Charlotte 🦝 
charlotte
the true solution to the open source supply chain is to commit every single thing ever written in any programming language and mint it on the ethereum blockchain
Charlotte 🦝 
charlotte
if plushies have a million fans, then i am one of them. if plushies have ten fans, then i am one of them. if plushies have only one fan then that is me. if plushies have no fans, then that means i am no longer on earth. if the world is against plushies, then i am against the world.
Charlotte 🦝 
charlotte
you can tell because i made it up and it's not registered anywhere
Charlotte 🦝 
charlotte
i wish programmers of bad name fields get their name rejected as invalid somewhere